Stalkerware Cases Stabilize, but Remain Concerningly High
How online creeping and cyber stalking differ, the most common cyber stalking tactics, and where we are with stalkerware today

How online creeping and cyber stalking differ, the most common cyber stalking tactics, and where we are with stalkerware today
Online creeping is extremely widespread nowadays—whether it’s checking a new colleagues’ LinkedIn, scrolling through a new love interest’s Facebook, or even perusing friends’ latest Venmo transactions out of curiosity—it can feel as though the access we have to each other’s day-to-day lives has no bounds. However, this level of access to personal details and whereabouts can quickly cross over into concerning territory.
For our third annual Norton Cyber Safety Insights Report: Special Release for Online Creeping, The Harris Poll surveyed over 10,000 adults across 10 countries to understand people’s attitudes and behaviors when it comes to online creeping and stalking—and we took a look at how that compares to the latest stalkerware cases.
Online creeping versus cyber stalking
While the majority of people agree there is at least some harm involved in stalking a current or former partner online, more than one in three adults surveyed globally who have been in a romantic relationship admit to checking in on their current or former partner without their knowledge or consent—and 22% say they would be more likely to stalk a current or former partner online if they knew they would not get caught.
This behavior, which we call “online creeping,” isn’t necessarily harmful. For example, when asked why they creeped on their partner online, 37% of those who have, said they were “just curious.”
But some had more charged reasons for poring over their partner’s digital life, including these:
- 40% of adults surveyed said they didn't trust their significant other or suspected they were up to no good.
- 36% said they wanted to know where their partner was or who they were with.
- Further, 26% of all adults surveyed said online stalking is OK if one or both partners have cheated or are even just suspected of cheating.
Online creeping behavior crosses over into concerning territory—or cyber stalking—when it becomes a pattern or evolves to include the use of technology and tactics to discreetly track someone’s personal activity or information in an invasive, often illegal, way.
Among adults surveyed globally who have been in a romantic relationship, the most common stalking behaviors were checking on their partner’s phone to view information like text message, phone calls, emails, or photos (17%), reviewing their significant other’s search history on one of their devices (13%), using knowledge of their partner’s passwords to access their device or online accounts, like social media profiles (10%), and tracking their location via a location sharing app (9%).
Alarmingly, 7% of them admit to using an app – i.e. stalkerware – to monitor their partner’s text messages, phone calls, direct messages, emails, or photos.
This data is in line with what we’ve seen at Norton Labs in examining stalkerware apps detected by Norton Mobile Security for Android, which uses a combination of reputation and machine-learning algorithms to flag apps that can be used for spying. As it stands, our research team has found that 1 in 13 Android devices globally were infected with stalkerware in the past year.
What is stalkerware?
The use of stalkerware apps is one manifestation of malicious cyber stalking. Stalkerware is best described as software that enables someone to monitor the activities on another person’s device without their knowledge or consent.
When someone installs stalkerware on another’s phone, they can gain access to that person’s personal device activity—such as location, text messages, phone calls, social media, and more. In most cases, the information is sent to the abuser’s email address or synced to a cloud account they can access.
While other applications might have some of these capabilities—like location-sharing with friends and family on Google Maps or Apple’s Find My Phone —these provide routine notifications and warnings that your device’s location is being tracked, which makes them difficult to use in secret. What differentiates stalkerware is that it’s installed by a third party without the consent or awareness of the device’s owner, often camouflaged by icons that falsely indicate a benign purpose like “Battery Saver” or “System Services” and without providing notifications of their presence on the device. Making matters worse, app launchers can be configured to hide the presence of the stalkerware app, rendering them invisible except in Android’s settings menus.
Stalkerware by the numbers
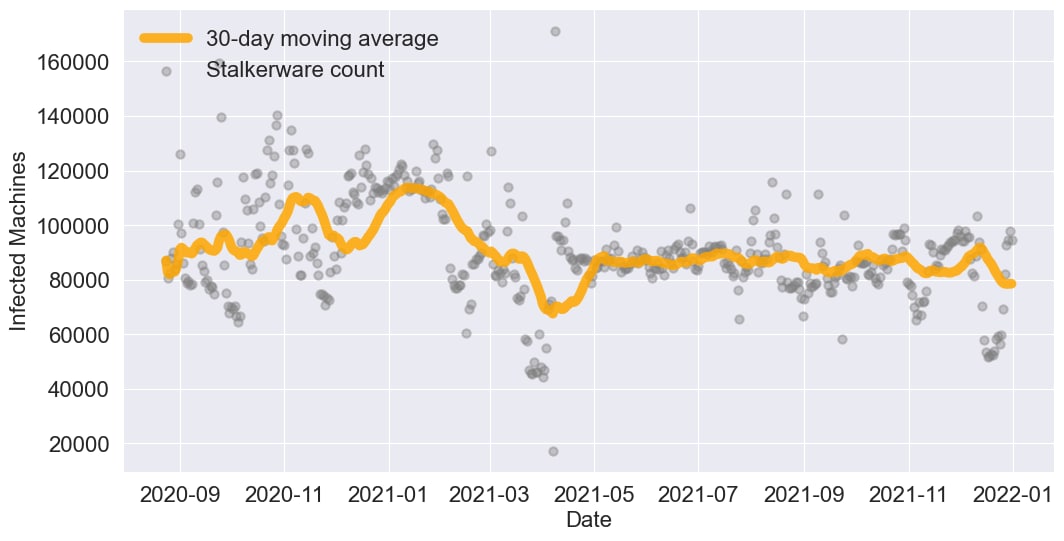
Figure 2: Daily number of Android devices reporting stalkerware from September 2020 through December 2021. Detections climbed by 42% from September to December 2021 and have since stabilized.
Our Norton Labs team has continued to monitor the number of devices reporting stalkerware samples on a daily basis using Norton’s stalkerware blacklist. While we saw a dramatic uptick in the number of devices infected with stalkerware in late 2020 and early 2021, numbers have held steady since March 2021. We hypothesize a few reasons that are at least partially responsible for this stabilization:
- We saw an upward trend in stalkerware as people went into lockdown, which forced many to spend more time at home, where personal belongings are easily within arm’s reach, likely creating more opportunities for perpetrators of tech-enabled abuse to install stalkerware on their partner’s devices. As lockdowns have subsided, it seems as though stalkerware installations have ceased to increase, though they remain at concerningly high levels.
- Following pressure from our Norton Labs team and other organizations, major app stores have banned apps that openly encourage prospective users to spy on their significant others’ phone and blocked overt search terms (e.g. “catch my cheating girlfriend” and “hidden call recorder”) curtailing ease of access to malicious apps.
In examining the 10 countries surveyed for our Special Report on Online Creeping, we found the following infection rates by country:
Country - Infection Rate
India- 10.49%
United States- 9.98%
Brazil- 8.50%
Australia- 7.48%
Italy- 6.80%
United Kingdom- 6.72%
New Zealand- 5.91%
France- 4.43%
Germany- 3.90%
Japan- 3.05%
Combatting stalkerware through partnerships
Familiarity with stalkerware remains low—our Special Release for Online Creeping found that 83% of adults surveyed are unfamiliar with stalkerware, with 13% somewhat familiar, and just 4% very familiar. This may seem alarming—if people aren’t familiar with stalkerware, how can they identify it or know what to do if they find it on
their device?—however, we believe meaningful progress in helping protect people from stalkerware comes from raising awareness with customer advocacy groups, lawmakers, law enforcement, and major platform providers, so they can hold developers accountable.
At NortonLifeLock, we have teamed up with other security vendors as a founding member of the Coalition Against Stalkerware to share resources and research, in addition to the National Network to End Domestic Violence (NNEDV) to support its Technology Safety program, Safety Net, which provides educational resources and trainings on tech-enabled abuse.
In 2020, Norton Labs reported more than 800 stalkerware apps on the official Google Play Store, leading Google to remove the apps and update its policy.
But despite industry-wide efforts, we’re still seeing stalkerware in major app stores in more covert and disguised forms.
Why stalkerware still exists on major app stores
While it’s easier for major platform providers to identify and take down overt stalkerware that spies on many device’s sensors and communications channels, more obscure, single-use apps slip by. Just last year, our Norton Labs team found that 82% of the apps that can be used for covert surveillance only monitor a single type of device sensor or communication channel—consequently, these apps are more successful in positioning themselves for benign use cases.
One of the most prevalent use cases can be found in the form of recorder apps. These are harmless when the app can only be initiated by the device owner on a call-by-call basis - but many of the most widely used call recorders are automatic, silently recording every single phone conversation and syncing recordings to the cloud. What’s worse, these apps typically provide no notifications to the user and can be hidden. While the developers have argued their apps are harmless, we must wonder why they lack such simple yet critical safety features to preventing tech-enabled abuse.
Even when it comes to parental control apps, our Norton Labs team firmly believes those that monitor device behavior in a hidden or secret way without the child’s knowledge or consent are problematic. While
parental supervision apps can be useful tools for helping protect children, it’s best for parents to have open conversations with their children about online safety and the precautions they plan to take—not only to establish trust with their children but also to prevent covert apps from being used to track the behavior of non-consenting adults.
It ultimately comes down to the notifications and ensuring device users of all ages are aware of any apps that could be monitoring their device behavior and communication—and it’s the responsibility of major platform providers to establish and enforce this policy for developers.
How to help protect against stalkerware
If you’re looking to take further steps to help protect against stalkerware, it’s always a good idea to install a security app like Norton Mobile Security for Android to monitor your device. This will scan for the presence of potentially unwanted apps and flag them to you so that you can make an informed decision about what’s on your phone. To learn more about Norton Mobile Security, visit https://uk.norton.com/mobile-security-for-android.
About the 2022 Norton Cyber Safety Insights Report: Special Release – Online Creeping
The research was conducted online by The Harris Poll on behalf of NortonLifeLock among 10,003 adults aged 18+. The survey was conducted November 15 through December 7, 2021 in Australia (n=1002), Brazil (n=1000), France (n=1001), Germany (n=1000), India (n=1000), Italy (n=1000), Japan (n=1000), New Zealand (n=1000), the United Kingdom (n=1000), and the United States (n=1000). Data are weighted where necessary by age, gender, race/ethnicity, region, education, marital status, household size, and household income to bring them in line with their actual proportions in the population. No estimates of theoretical sampling error can be calculated.
All sample surveys and polls, whether or not they use probability sampling, are subject to multiple sources of error which are most often not possible to quantify or estimate, including sampling error, coverage error, error associated with nonresponse, error associated with question wording and response options, and post-survey weighting and adjustments. Therefore, The Harris Poll avoids the words “margin of error” as they are misleading. All that can be calculated are different possible sampling errors with different probabilities for pure, unweighted, random samples with 100% response rates. These are only theoretical because no published polls come close to this ideal.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.




Want more?
Follow us for all the latest news, tips, and updates.